
CMMC 1.0 vs CMMC 2.0
The following blog is the first from our latest partner, Atomus Corp. Atomus helps small and medium sized businesses comply with defense industrial base specific cybersecurity requirements such as NIST 800-171, DFARS 7012, ITAR, and CMMC. Atomus’ unique technology helps businesses get cyber secure and auto-generate compliance paperwork needed by primes and the military to pass cybersecurity audits and questionnaires. Aerospace and defense contractors across the country trust Atomus to keep their organization cyber secure and compliant in addition to the US Air Force, Space Force and Marine Corps.
The Cybersecurity Maturity Model Certification (CMMC) is a requirement many defense contractors have on their radars. A recent change published in November of 2021 rolled out CMMC 2.0, an updated version of the CMMC requirement.
The Department of Defense has made cybersecurity a top priority within the Defense Industrial Base. Cyberattacks have become more complex and frequent with technology and sophistication of attacks increasing exponentially. As a result, the Department of Defense has been rolling out requirements for defense contractors in their supply chain to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). The Cybersecurity Maturity Model Certification is the updated requirement for how companies need to protect FCI and CUI in order to do business with the Department of Defense.
What Was CMMC 1.0?
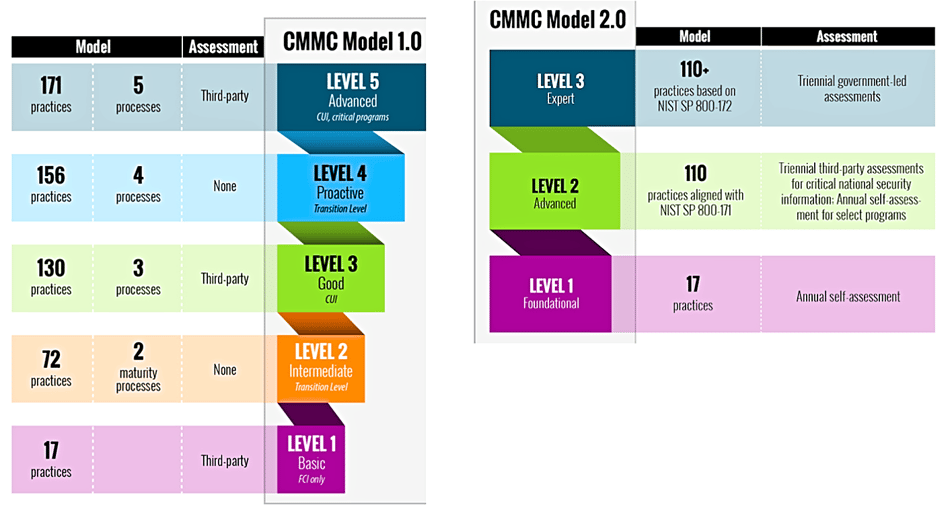
CMMC 1.0 had 5 different levels (Level 1-5) which every defense contractor would be categorized into. Based on the level a specific defense contract would be assigned by the contracting officer, the contractors would need to meet that level of requirements. As part of CMMC 1.0, the government proposed requiring third party cybersecurity audits to verify companies were in compliance with the regulation.
What Is New In CMMC 2.0?
Most of the changes were aimed at making the CMMC regulations simpler for small businesses. Most of the new CMMC regulations will still affect businesses who hold Controlled Unclassified Information and most likely have a DFARS 7012 clause in their contract. At risk of oversimplifying the changes, for small businesses the big changes were the following:
- CMMC 2.0 cut the number of levels from 5 down to 3 so now there are only levels 1-3.
- Instead of requiring audits for all companies, CMMC 2.0 requires third party audits for
levels 2-3. These companies are the ones who hold Controlled Unclassified Information. - Reducing the number of additional cybersecurity requirements made specific for CMMC.
Level 2 companies will be audited against the existing NIST 800-171 standard as
opposed to the NIST 800-171 plus the “Delta 20” processes that were additional in
CMMC 1.0.
Atomus customers don’t need to worry about these changes as our software automatically updates to ensure they are compliant with the latest regulations.
What Does CMMC 2.0 Mean For My Business?
CMMC is still going through the rulemaking process. As a result, it may be until late 2022 or early 2023 till the requirement is first seen in contracts. Our advice for defense contractors, specifically businesses that work with Controlled Unclassified Information, is to focus on the existing cybersecurity requirements in your contracts. The Department of Defense is getting more strict on cybersecurity and enforcing the existing requirements that are in contracts.
For companies that work with the Department of Defense, this comes in the form of Supplier Portal Risk Scores that rate what percentage of the NIST 800-171 requirements your company has implemented. For companies that work as subcontractors, major prime contractors have started rolling down cybersecurity questionnaires asking if companies are compliant with NIST 800-171 requirements which are included in the DFARS 7012 clause that is flowed down in their existing contracts with subcontractors.
From a prime contractor’s point of view, they are looking to hedge against risk in their supply chain when it comes to cyber attacks on their supply chain and compliance requirements that may disqualify suppliers in the future. As a result, we have seen examples where companies have lost reliable long term work because they weren’t compliant with existing cybersecurity requirements let alone future CMMC requirements.
If you are looking to better understand these requirements and how they may apply to your business, reach out to our team at Atomus today.
Atomus will be publishing future posts on DFARS 7012, NIST 800, and other relevant cybersecurity compliance topics on both the ReliAscent Blog and the Atomus Blog, so be sure to subscribe to both and keep an eye out for their next installment!